Sws101_journal3
Topic : OWASP Top 10 - 2021: The OWASP Top 10 vulnerabilities and the most critical web security risks.
The OWASP Top 10 is a classical security awareness document that is developed by the Open Web Application Security Project (OWASP). This component is the backbone of the whole OWASP Top 10 that represents the common consensus about the most dangerous web application security problems that should be tackled by the security organizations.
The 2021 edition of the OWASP Top 10 lists the following high risk issue areas:
- Broken Access Control
- Cryptographic Failures
- Injection
- Insecure Design
- Security Misconfiguration
- Vulnerable and Outdated Components
- Identification and Authentication Failures
- Software and Data Integrity Failures
- Security Logging and Monitoring Failures
- Server-Side Request Forgery
The goal for this learning is to educate developers, designers, architects, managers and organizations about the consequences of the most important web application security weaknesses. Understanding the risks is the first step towards mitigating them and making web applications more secure.
The learning platform of the Top 10 vulnerabilities is Try Hack Me site where it provides a hands-on approach to learning about these vulnerabilities and how to exploit them in a safe lab environment. The walkthrough covers different vulnerabilities and tasks related to web security. Thus, I gained the practical experience in identifying, exploiting, and preventing these common security weaknesses.
The learning outcomes for each task in the brief:
Broken Access Control (IDOR Challenge): Understand the impact of Insecure Direct Object References (IDOR) on application security, the importance of proper access control mechanisms, and the risks of exposing sensitive information through improperly secured endpoints.
Cryptographic Failures: Understand the importance of securely handling and storing sensitive data, the process of cracking password hashes, and the risks associated with weak or compromised passwords. This task also emphasizes the need for secure cryptographic practices.
Injection: Gain experience in identifying and exploiting command injection vulnerabilities, understanding how to execute arbitrary commands on the server, and the importance of input validation and sanitization to prevent such vulnerabilities.
Insecure Design: Gain insights into exploiting weak password reset mechanisms, the importance of securing sensitive information, and the risks associated with insecure design practices. This task highlights the need for robust security measures during the design phase of applications.
Vulnerable and Outdated Components: Learn about the risks associated with using outdated or vulnerable components in applications, the process of identifying and exploiting known vulnerabilities in these components, and the importance of regularly updating and patching software components.
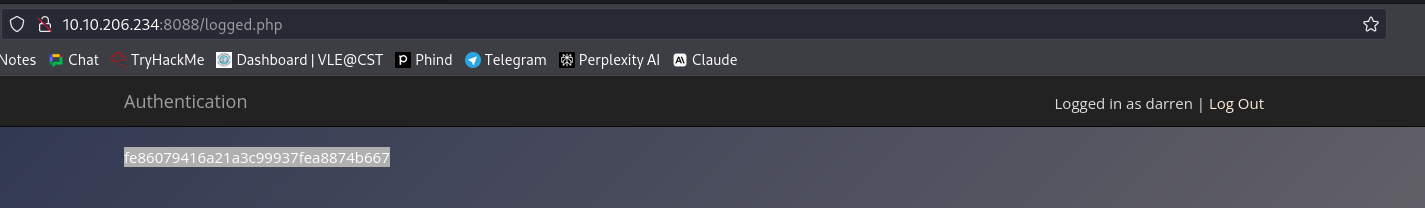
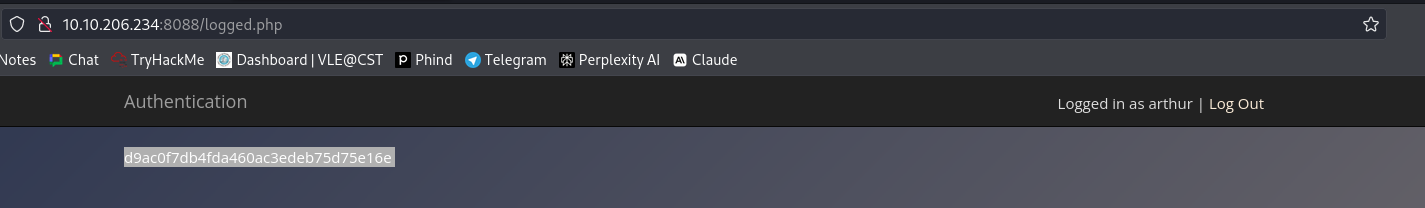
Identification and Authentication Failures: Learn about common vulnerabilities in identification and authentication mechanisms, such as weak password policies, the importance of secure password storage and verification, and the risks associated with insecure authentication practices.
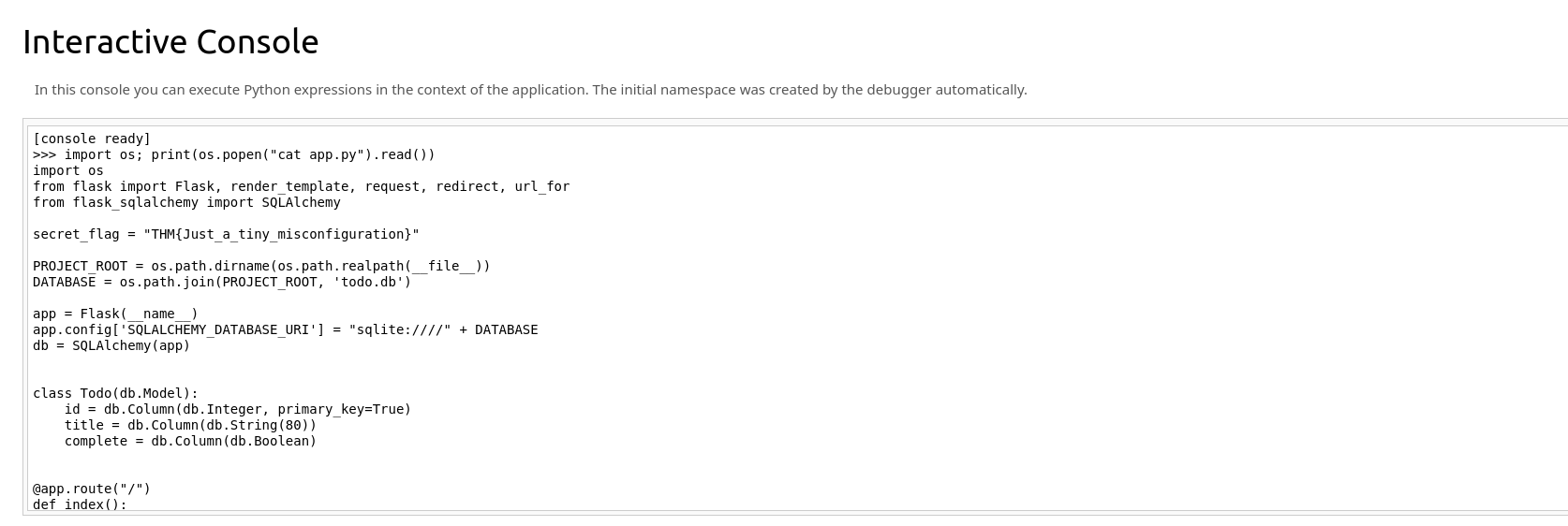
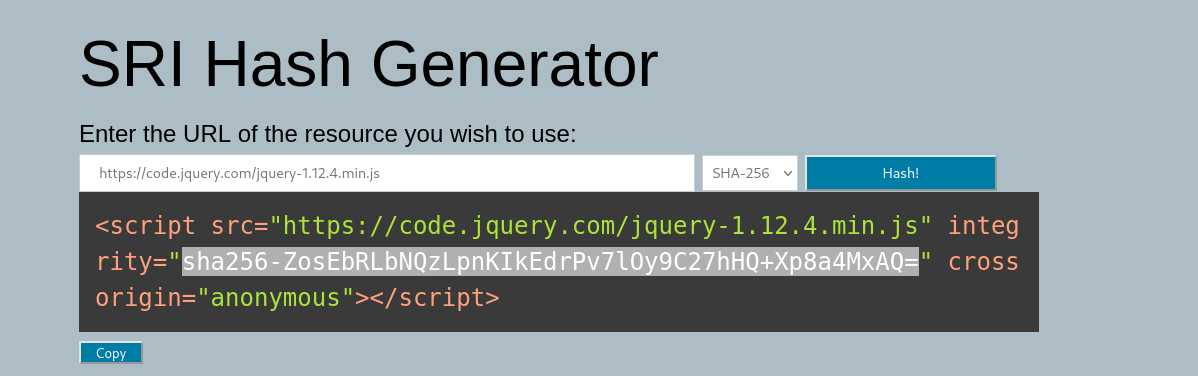
Software Integrity Failures (Security Misconfiguration): Learn about the importance of verifying the integrity of external resources, the use of Subresource Integrity (SRI) for ensuring the integrity of web resources, and the risks associated with not verifying the integrity of external resources.
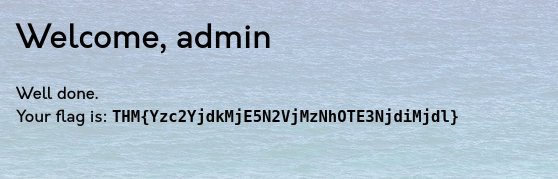
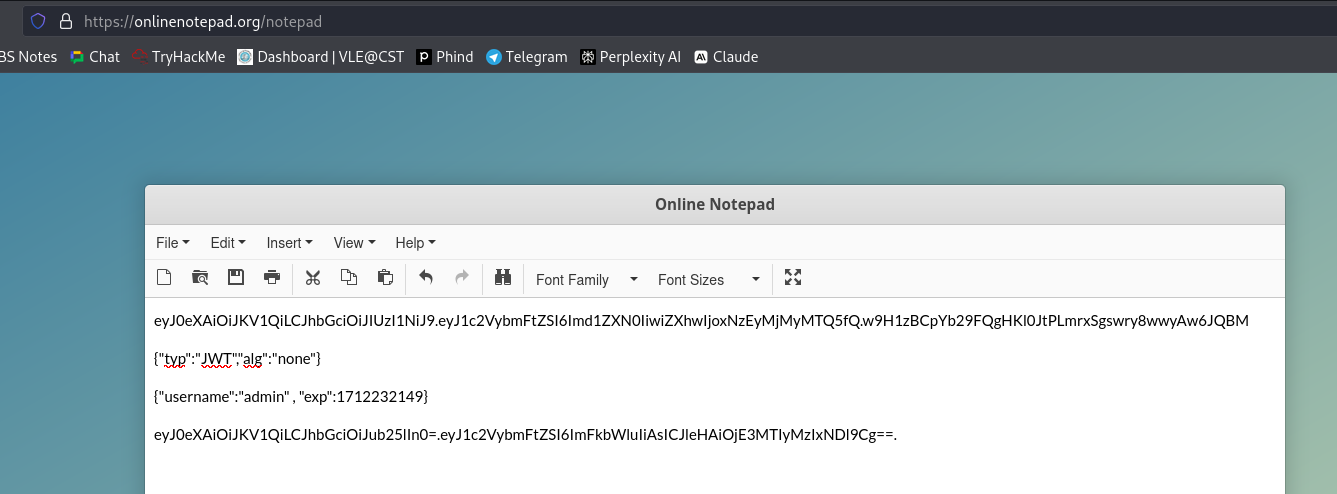
Data Integrity Failures: Learn how to manipulate JWT tokens to change user roles, understand the structure of JWT tokens, and the importance of validating tokens on the server side. This task also emphasizes the need for secure handling of authentication tokens.
Security Logging and Monitoring Failures: Learn about the importance of effective logging and monitoring for detecting and responding to security incidents, the identification of suspicious activities through log analysis, and the need for timely action to mitigate security threats.
Server-Side Request Forgery (SSRF): Gain insights into the SSRF vulnerability, understand how to exploit SSRF to access internal resources or perform actions on behalf of the server, and the importance of validating and sanitizing input to prevent SSRF attacks.
Getting Started
1. Broken Access Control
It represent a major security issue by enabling third parties to get hold of information they are not supposed to or to use the functionalities that are available only to authorized individuals. This specific weakness has the potential to result in serious incidents, such as obtaining private data, unauthorized activities, and the security breach of user privacy and the restricted accessing of the system. In a well-known case, it was shown that YouTube has access control problem that allows for style frame extraction. In other words, individual private frames are taken, and the whole video is put together in a way that the user is meant to see, yet the attackers are able to access and use the video which they were not supposed to view. Amid this breach, this underlines the security of reliable systems to preclude unauthorized access to confidential data and key similar functionalities. Beside that, User data manipulation, service disruption, and other harmful activities may be carried out by the broken access control leading risk for users data and system integrity, so all-encompassing security measures should be implemented to shield users data and system stability.
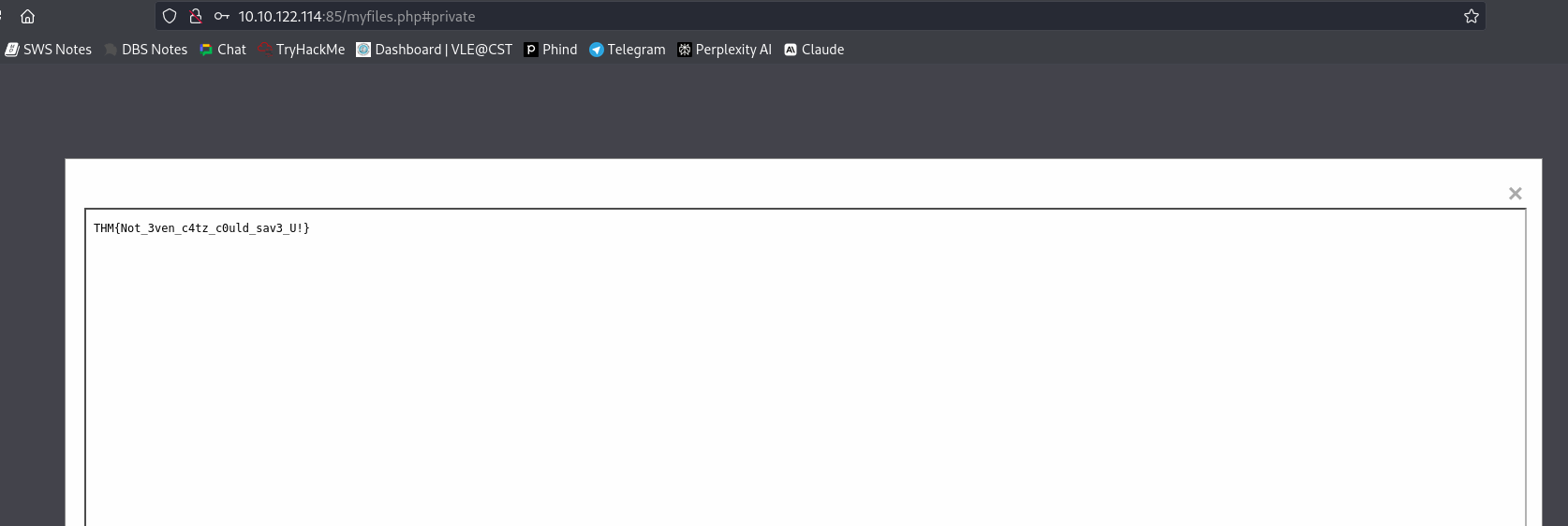
The vulnerability is Insecure Direct Object References (IDOR): Humans may be prone to make predictable movements in URLs or other references that may be missed by the intruders and hence access unintended resources. As an example, if a user ID is revealed through a URL to access an account and its profile, a hacker would be able to tamper with their own link by generating a custom URL to get another user’s profile. IDOR Insecure Direct Object Reference occurs when the application just provides the direct reference of any internal object such as Document, User account and Data base records without properly validating users access rights. With vulnerability the attacker can access and modify resources they should not be able to even by changing a reference for example a parameter in a URL address.
The problem is that the application doesn’t ensure that the authenticated user has the rights to see the requested object is not checked. Thereby, an attacker can trick a user to the revealing sensitive data by manipulating the reference of direct object.
To mitigate this vulnerability, applications should implement proper access control mechanisms, such as verifying that the authenticated user has the necessary permissions to access the requested resource before granting access. Additionally, direct object references should be obscured or randomized to prevent easy guessing or manipulation by attackers.
2. Cryptographic Failures
Cryptographic failures also known a significant security risk, are exposed when protection through cryptographic means is not done in the first place, hence information such as passwords, and financial data is not cryptographically secured. These problems can originate from diverse sources- an example, unsafe data base benefits, mistakes in configurations, flaws in software, low level encryption, or inadvertent uploading. Cryptographic errors obviously are important since they affect both the private lives and business of individuals who lose personal details, financial information, or become potential targets of identity theft or fraud. The cryptocurrency flaws exposed by the Exactis Debacle and the Facebook event had been due to cryptographic failures. These included cases where data such as sensitive information had been exposed due to either weak encryption or misconfiguring networks. For avoiding cryptographic failures it is vital to use Cryptographic functions carefully, avoid deprecated algorithms and, utilize secure communication protocols like TLS/SSL on data transmission.
Their vnlnerabilities:
Insecure or Weak Algorithms: Cryptographic algorithms are the mathematical formulas, which convert the data into a cipher text and vice versa. Employing old algorithms with poor or clumsily built cryptographic mechanisms will make it even a step easier for hackers to de-crypt the information and get to the owner.
Improper Key Management: Encryption keys are like the password for your encrypted data. Weak or bad key management means that encryptions are no more effective.
Missing or Improper Encryption: No encryption of data at rest (on servers) or in motion (transmitted over networks) leaves it subject to anyone who can access it.
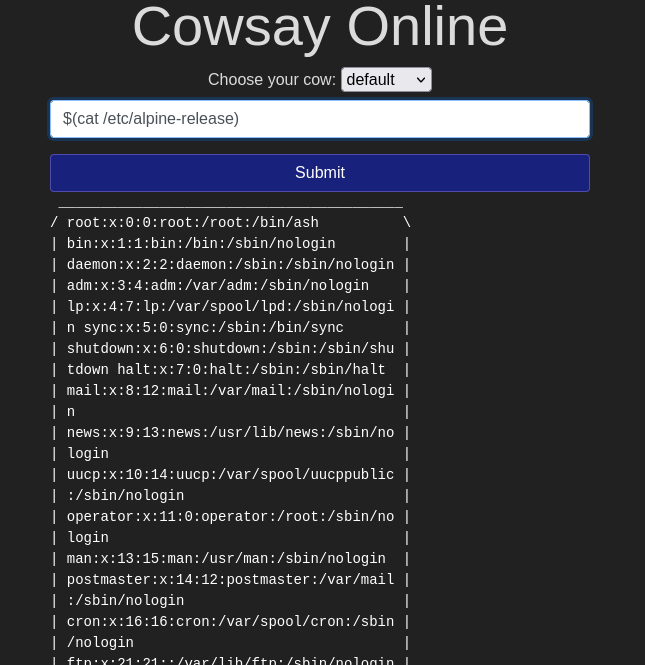
3. Injection
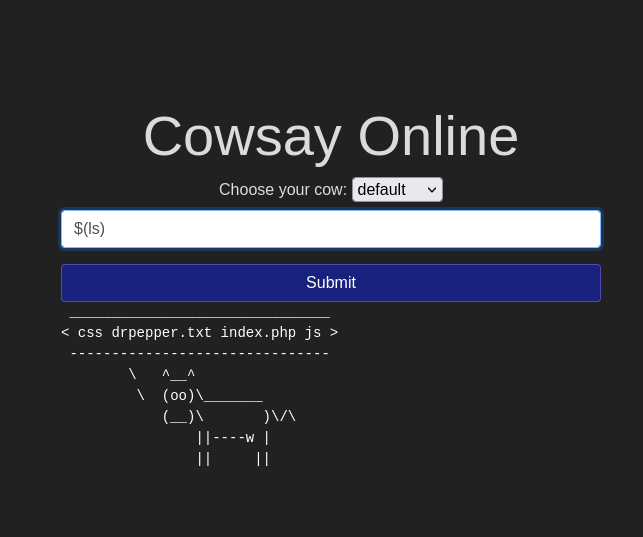
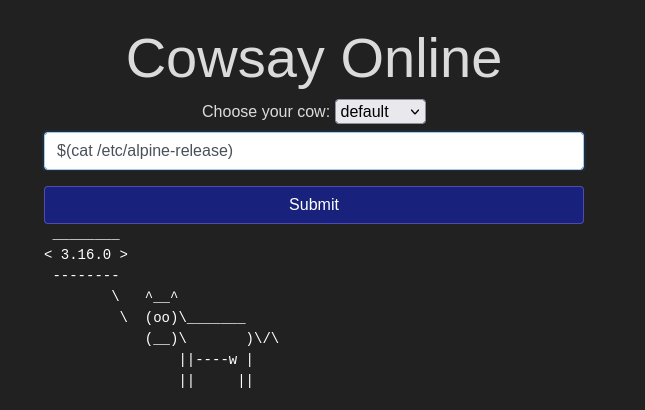
Injection flaws are prevalent in applications from users’ misunderstanding of the commands or data they have submitted. These flaws grant an access to SQL Injection or Command Injection attacks, when an attacker attempts to manipulate a query or system command, and as a result can read, modify or delete information that was until then only restricted to certain users. Here the risks of interaction can be eradicated by a user-control of the data input which is not be seen as requests or commands. It can be carried out in many ways, for example: by the means of employing the allow list to compare input against the safe input list, stripping of dangerous characters before further processing, or using the libraries to perform them automatically. Implementation of prepared statements via parameters, utilization of stored procedures and application of restriction over database access are among defensive strategies that can fight sql injection. These tactics help stop the malicious SQL input from being included in executed input checks, thereby bring a security barrier against injection attacks.
Command injection: are a web application vulnerability that can be exploited for injecting unauthorized operating system commands, thereby gaining administrative privileges.
This vulnerability occurs when the platform fails to validate or sanitize user input before executing system shell commands, which can lead to exploitation at the medium or even the highest level. The attacker can do this either by injecting malicious code as part of the input or by means of another input parameter. Thereby he can get the application to run commands that it was not originally intended to, which could lead to unauthorized access, theft of data or system compromise in the worst case.
Proper input sanitization, avoiding the use of insecure functions that interact with the system shell, and implementing robust access controls are essential to mitigate this vulnerability.
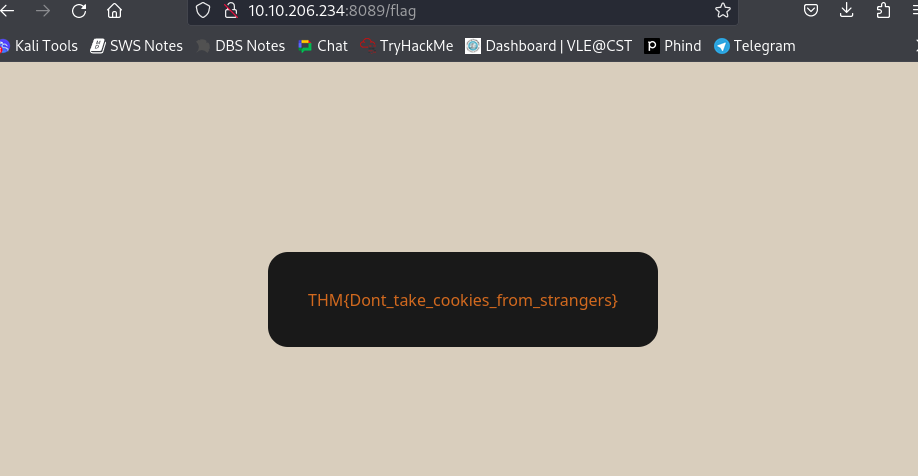
The final flag:
4. Insecure Design
Insecure design, as a breach of security, is one of the vulnerabilities which are caused by drawbacks that exist during the web application design and architecture process, and they can lead to breach of security or data leaks.
Usually this risk comes from the poor threat analysis performed during the planning and design stages of software development. In some instances developers even might introduce them onto the production environment unintentionally when they either implement “shortcuts” or bypass security features in order to make the bug detection easier yet neglect to transition back before production deployment.
To mitigate such risks, It is to follow secure design principles and do threat modeling in detail during development that perform beforehand in the development lifecycle where Secure Software Development Life Cycle (SSDLC) is taken as reference for best practices.
5. Security Misconfiguration
Security misconfigurations involve cases when security settings are not correctly enforced or configured in network protocols, hardware, software and databases. Thus, systems remain vulnerable despite using the latest software versions. Common examples include:
- The inaccurate cloud service account permissions (such as public S3 buckets) are among the most significant challenge.
- Extra buttons, boxes or accounts which are not necessary on the home page.
- Default login with out customizing passwords.
- Supplemental error messages added in the platforms reveal system’s unnecessary details.
- Missing HTTP security headers
Leaking of these configuration mistakes can occur, resulting in other vulnerabilities exposed for example, default credentials allowing access to sensitive data or deliberately designed functionality such as XML external entity (XXE) and command injection. Security misconfigurations differ from other vulnerable points because security could have been rightly established, but something done or omitted made the systems improperly secured. Solutions to these challenges include doing a thorough jobsite and IT security hardening evaluation and putting implemented hardening into place.
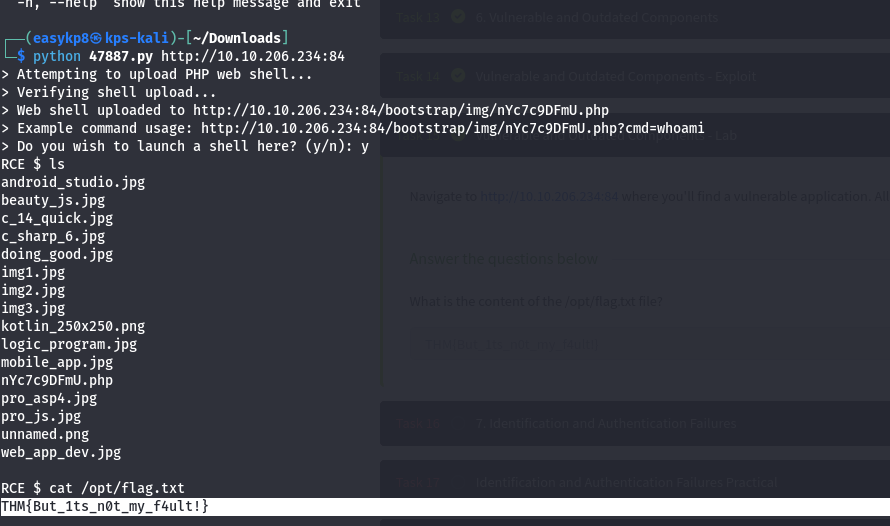
6. Vulnerable and Outdated Components
In web applications is the key problem that makes them highly susceptible to hackers` attacks in which the intruders would easily get unauthorized access or control over systems. The forthcoming technologies often have saved some security glitches that hackers can use for their advantage, e.g. code injection, buffer overflow and cross-site scripting. Obsolescence of components, usually, is not supported by their manufacturers, thus, the system cannot be patched with latest security patches as the vulnerabilities keep emerging. Hence, such dated systems become easy targets for cyber attacks.
There are nevertheless risks of using version control systems that should be mitigated. It is, therefore, important that components of these systems are regularly updated with security updates or patches from their developers and use only active and maintained components developed by an active community of developers. Monthly security scan with automated tools in use, asset repository to contain all third-party libraries and frameworks, and security advisories from components developer are also the vital best practices for vulnerable and outdated component management.
7. Identification and Authentication Failures
They are the vital elements in web application security which facilitate controlled access to resources for validated users and secure management of sessions. Authentication often involves verifying users identities utilizing the username and password mechanisms while session control involves session management which deals with user sessions after username and password authentication. The two main shortcomings inherent in authentication mechanisms are:
- Brute-force guessing,
- Weak passwords
- Predictable token codes in session cookies.
Issues of this kind can only be waved aside if strong password rules are enforced, if lockout password after more than three failed attempts is applied, and if multi-factor authentication is employed. Particularly, implementing robust session IDs, setting sessions to expire after a defined span of inactivity and employing HTTPS for SSL encryption are the key aspects to be considered for session management.
Surveillance of suspicious activities, for instance, repeated login attempts from unique IP addresses, is one of the approaches which can be utilised to thwart evasion of attacks. Authentication and session integrity proofing are essential to protect web apps from threats and which warrant the fact that solid and unbreakable security mechanism must be implemented.
8. Software and Data Integrity Failures
The data integrity , which is a fundamental rule of cyber security, seeks to ensure that data carries throughout the cycle of life without being edited or corrupted The data is converted hashes or digests or unique numerical values developed as a result of applying algorithms like MD5, SHA1, and SHA256 along the data. However, these hashes are digital fingerprints which can be used as a verification tool to compare the calculated hash of an acquired file or data set to the published hash of the source data.
Among other things, this comparison also applies whether or not data has got lost, been made up or erased during the transport of data or when it was stored. Demasque con fails on data integrity when software or data is used without performing integrity checks like already attacked by attackers without authorization. These deficiencies can be grouped into two types of software integrity failures, they are modification of the running code, and data integrity failures, a change to the input data.
The use of techniques such as hashing to preserve data integrity is essential to software, files, or data which are authentic and trusted to prevent intentional corruption caused by cyberattacks and the unexpected behavior which may result from failures in data integrity, leading to security breaches.
9. Security Logging and Monitoring Failures
The role of logging and monitoring cannot be overstated when it comes to web application security. As logging and monitoring are a cornerstone of any proper mitigation strategy which allows for detection and response to potential threats.
Logging is fundamentally critical for the tracing of attacker activities and the assessing the risk and the impact of security incidents, which log is normally thorough in indicating HTTP status codes, time stamps, usernames, AP endpoints, page locations and IP addresses. This is the data that can be used for many reasons, such as investigating an incident, adhering to regulatory requirements, and even stopping the attack after a breach.
On the contrary, monitoring is crucial for spotting in real time of potential dramatic initiatives including unauthorized access attempts, suspicious IP addresses, usage of automated tools as well as defined attack payloads.The identified activities are rated according to the potential level of impact, the higher level of impact result in alarm so responses can be done immediately. Highly secure log storage in multiple locations as well, with the possibility that logging records may contain sensitive data, must be taken into account.
10. Server-Side Request Forgery(SSRF)
SSRF is a vulnerability that happens when a web application unintentionally makes requests to other servers based on the demands of an attacker, whose traffic is still processed with a server’s original IP address. The weakness often arrives when the software that has to interact with third-party processes or APIs comprises parameters which are user-controlled and indirectly, this determines the target server
As an example given on reading material, an API may request for the “server” parameter to be set which must point at the SMS service provider’s server. Yet, hacker by modifying the parameter will send traffic to a server he/she owns in the process which will lead it to forward any secret data (including API keys) for the attacker to spy on.
SSRF vulnerabilities can be exploited for various purposes, such as:
- Conducting discovery of the internal network, IP addresses, ports.
- Blaming on the server enough to access the forbidden services is an example of that type of abuse.
- An attacker can use a non HTTP service to achieve this exploit thus creating a situation where remote code execution (RCE) becomes possible.